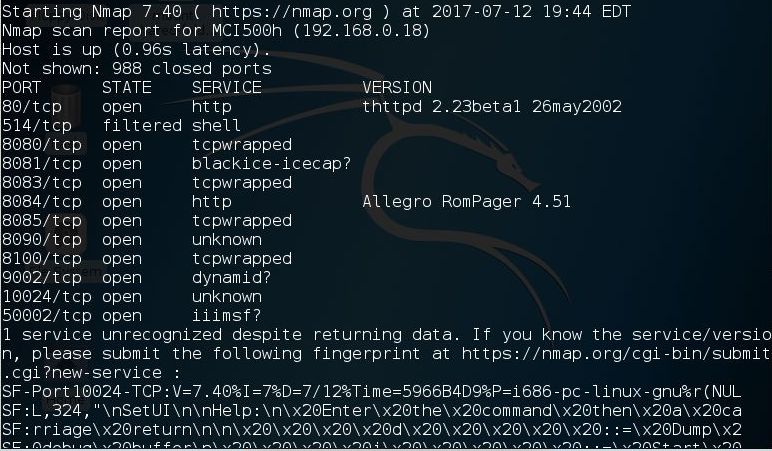
NMAP and Advanced Port scanner found almost the same port :
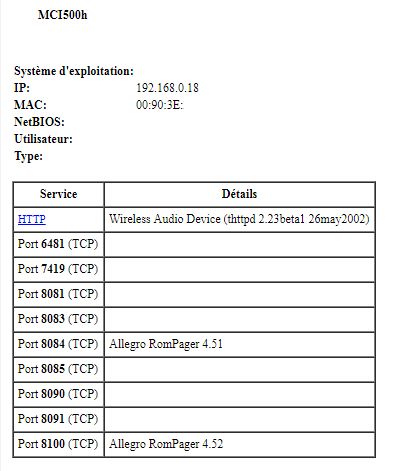
I bought these 2 devices some years ago because they were the only devices which used upnp/dlna correctly at that time (on a side note, it seems it's always the case!).
I really like these devices but there are some things which bug me :
I can't say I'm a hacker, but I bought these devices, Philips don't seems to spend any more dollars on it so it's my duty to try to fix these issues myself...or stop complaining about them !
Personally, it was a real great surprise to find Philips giving easily access to the open source part of their devices for anyone asking for it
I so asked the sources related to my 2 devices
Of course, some lib are proprietary but it will only slow me a little ;)
Hopefully, some people already did initial works which save me some months of test-and-try session:
Penma got the same problem on radio station and found how his device talk with www.ecdinterface.philips.com. He though the communications were encrypted and bet they were using RC4 but stop his analysis there
Koen Van Impe went a little further : he analyzed packets between his TV and http://www.ecdinterface.philips.com:80/perl/ecdav using Zap, an awesome scriptable web proxy.
Thanks to this we know a Session-Key is needed (starting from 0001000 to XXXX0000) on HTTP header and the POST parameter is a eui64=XXXXX&args=encoded_data
SmallHack got root access to his MCI730h and checked its MTD partitions. The part7 is interesting for people who know what it could mean : "ECD_key". He also asked and received the OSS from Philips which help him to make some awesome hacks.
Simon Kagstrom, after some raw hacks, asked too the Open-source software to Philips and shared it to the web . It seems he also made some hacks, available on his githup repositories (but infos are on different parts of the web it seems)
If you read the article about Streamium at wikipedia, you'll learn ECD Interface is in fact the backend for all Streamium services.
But in fact, it's even more : it's the backend f almost every connected Philips devices, from TV to Hifi, from Bluray player to fridge (!).
If you know how communicate with ecdinterface.philips.com, you'll be able to fake it.
My goal is only to control the radio list, that's all, I won't go further so don't expect to find a way to get VOD on your TV for 0$ !
The ECD communication is first initialized when you register, like on this video:
Thanks to Koen Van Impe, I know I need to find how is encoded the POST parameters.
The MCI730 OSS include the libecd.so library, which seem to be exactly what I need to investigate
Thanks to my favourite tool, IDA, I quickly found references to the infamous www.ecdinterface.philips.com and subdirs, which confirm I'm on the right path.
I'm now looking for the way it is encoding data.
I'm pretty sure it use the ECD_Key but needs to know which cryto method it really uses and if the key is part of the data on saved on both : ECD server and ECD_Key partition, with MAC address as unique identifier.
Another way to analyze a system is to inspect its firmware update
devttyS0 is perhaps the most infamous user of this method.
He even went as far as to create a tool to automatize the unpack process, to get access to useful files : binwalk
Still available : last version(v1.17)
Before trying to hack anything, the basic thing to check are the ports of the device.
NMAP and Advanced Port scanner found almost the same port :


One thing to note is the 8100 port. It seems to be available according what the device is doing.
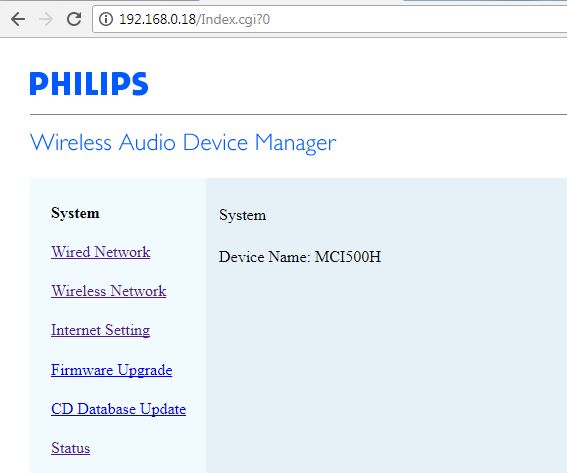
Classic http access to the device, it let you configure it..even the proxy which is the very useful feature for our need ;)
Only major problem : totally not secure !
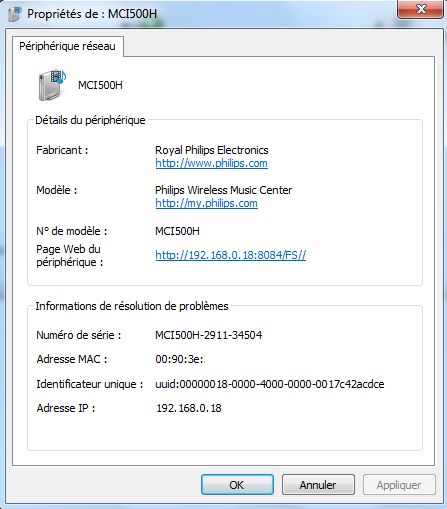
One of the (several) bugs with this device : a wrong UPNP configuration.
The initial configuration is to get the UPNP signature at : 8084/FS//
First, why /FS// and not /FS/
Second, there is absolutly nothing at this url :
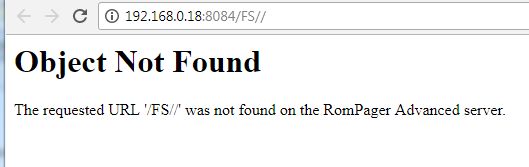
In fact, you should check on root to get something :
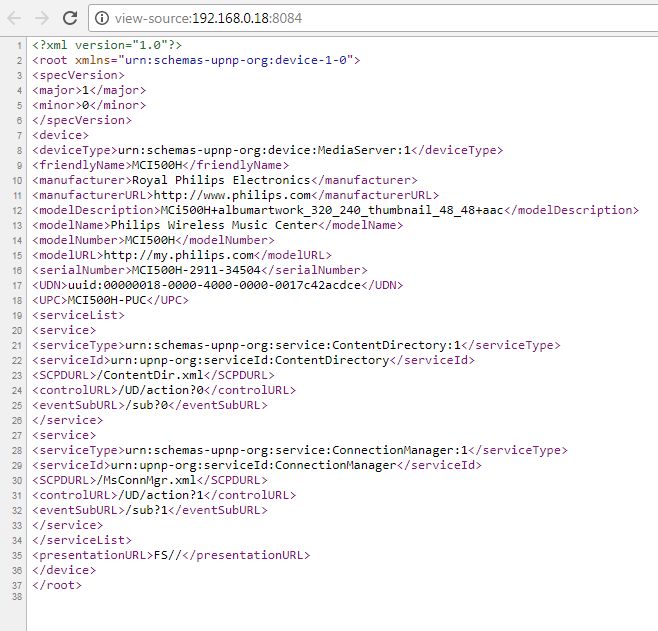
You'll nothice that the presentationURL is wrong (which explain the wrong url on Windows's properties screen)
More on UPNP later....
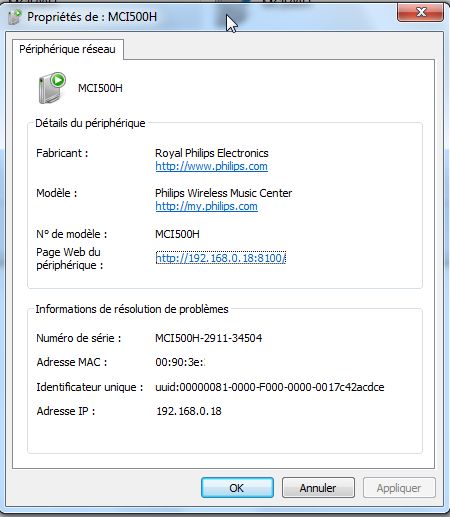
Second UPNP port.
This time, nothing wrong :
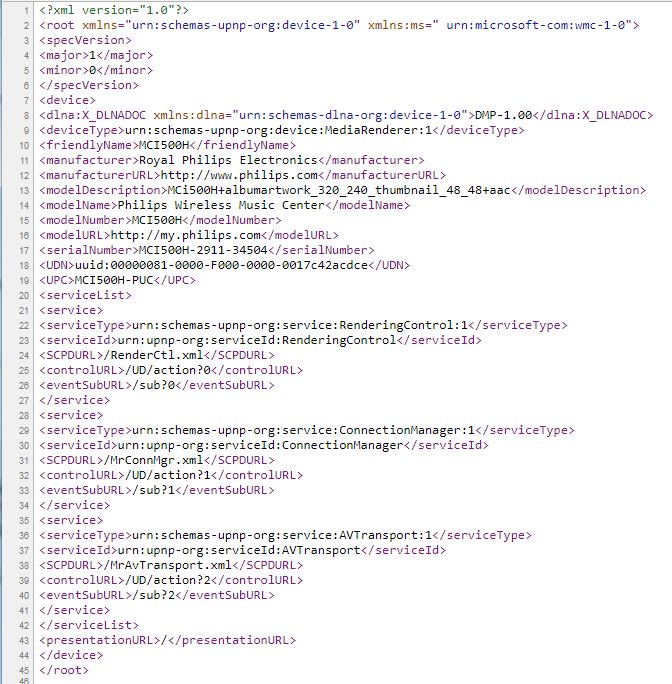
But you'll notice this UPNP presentation is bigger than the one at 8084
Again, more on UPNP later....